Configure Tunneling in DCC webgate:
- This is the key step in configuring the DCC HTTP reverse proxy
- Login to OAM Console and navigate to Application Security -> Agents
- Search for the agent registered for DCC Webgate operations
- Add the following user defined parameter in the Webgate configuration.
- TunneledUrls=/oam,/oamfed
- Now lets configure the policies for the required tunneled resources.
- Go to application security -> Application domains
- Search for the application domain associated with DCC Webgate
- Go to authentication policies
- Lets unprotect the following resources with anonymous authentication scheme
- /.../*
- /oam/.../*
- /oamfed/.../*
- In order to unprotected them, create a new authentication policy as 'Public Resource policy' which requires 'Anonymous Authentication'
- Create a new authorization policy for unprotecting the resources as shown below.
- Now add the resources to these authentication and authorization policies.
- With the above step, we have finished configuration of DCC Reverse proxy setup and we can validate now.
Validation:
- Access the protected resource http://<dcc_host>:<dcc_port>/dcc/dcc.html and authenticate to the resource. Once authentication is successful, you will be landing on to the protected resource.
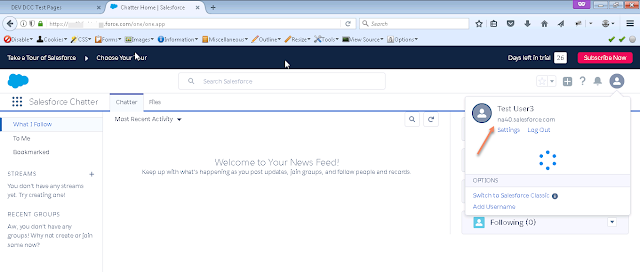
- Now access the IDP Initiated URL for Salesforce application with dcc_hostname and port in it.
- https://<DCCHost>:<DCCPort>/oamfed/idp/initiatesso?providerid=https://saml.salesforce.com
- You should be SSO'd to the salesforce now without authentication anymore.
So if you observe the URL above, /oamfed is the resource that is being served by the DCC Reverse proxy Webgate without adding any reverse proxy redirection on the webserver. This is the new tunneling introduced to enable the federated sign-on to partner applications.
Thank you for visiting.