This post specifically covers about configuration required to enable Encryption of SAML Assertion. Assuming we already have configured SSO to Service Provider application in SP Initiated mode which is Salesforce in our example.
Environment:
- OAM 11.1.2.3BP07
- Salesforce
- RHEL6/OEL6
- In this post, we are going to use the Self-Signed Certificate that can be generated inside Salesforce. In real environments, we usually get these certificates signed by third party certificate authority.
- Lets login to Salesforce application to create a Self-Signed certificate
- Go to Setup -> Ceritificates and Key management
- Click on Create Self-Signed Certificate to create new certificate if there is no existing certificate
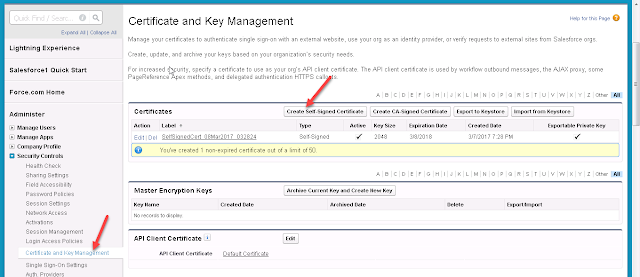
- Once the certificate is created, Lets configure the IDP Profile to configure the encryption settings.
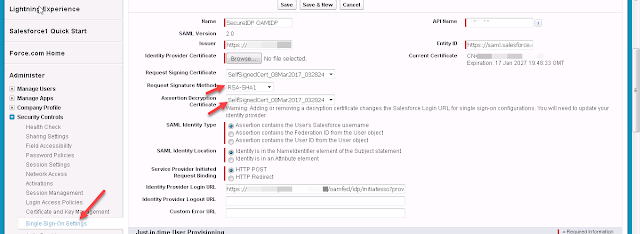
- Navigate to Setup and search for Single Sign-on settings
- Update the following options
- Request Signature method -> RSA-SHA1
- Assertion Decryption Certificate -> Select the previously created self-signed certificate
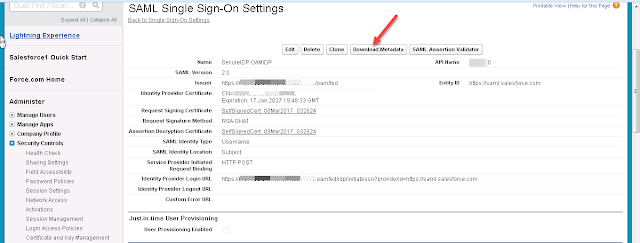
- If you compare this latest downloaded metadata with earlier, this will have additional information about the encryption information.

- Now we need to import this latest metadata into Identity Provider which is OIF
- Login to OAM Console and Go to Federation -> Identity Provider Administration
- Open 'Salesforce' service provider profile
- Click on 'Load metadata' to import this new metadata configuration
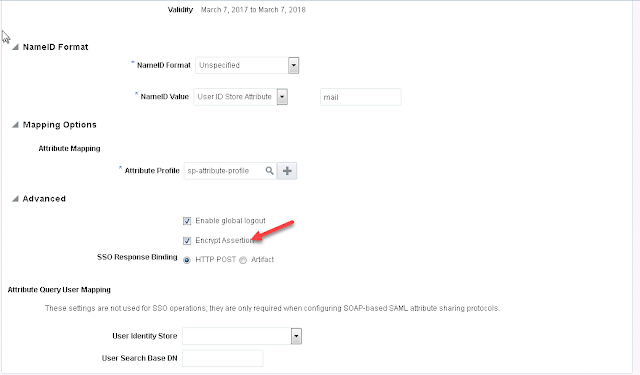
- Go to Advanced section and check the 'Encrypt Assertion' setting
- Save the changes made to this service provide profile.
- Ok. We are now finished with the configuration changes. Let's validate the Encryption now.
- Access the Salesforce application using the SP initiated URL.
- https://<mydomain>.my.salesforce.com
- This will redirect to the IDP Url to authenticate against IDP
- Provide the login credentials and click on Submit to login
- Once the authentication is successful, OIF engine generates SAML Response in encrypted manner as shown below. You can view this SAML messages using the browser plugins.
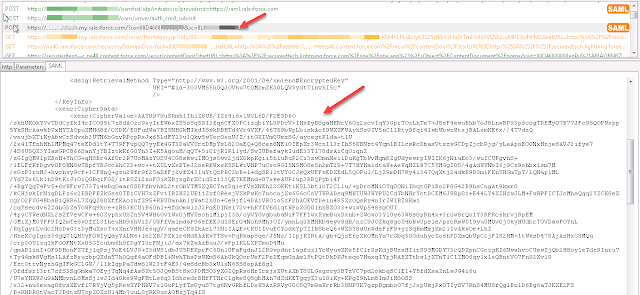
- Once the Assertion is successfully decrypted and validated by Salesforce, you will be landed into your Salesforce domain.
Thank you for visiting.